API Authorization
The Victor Platform leverages JSON Web Tokens (JWTs) to identify clients and to ensure the security of requests. In order to generate a JWT, the following requirements must be met:
- API Key must be generated from the client account
- Securely stored private key must be created (this client private key is not recoverable after initial generation, so don't lose it!)
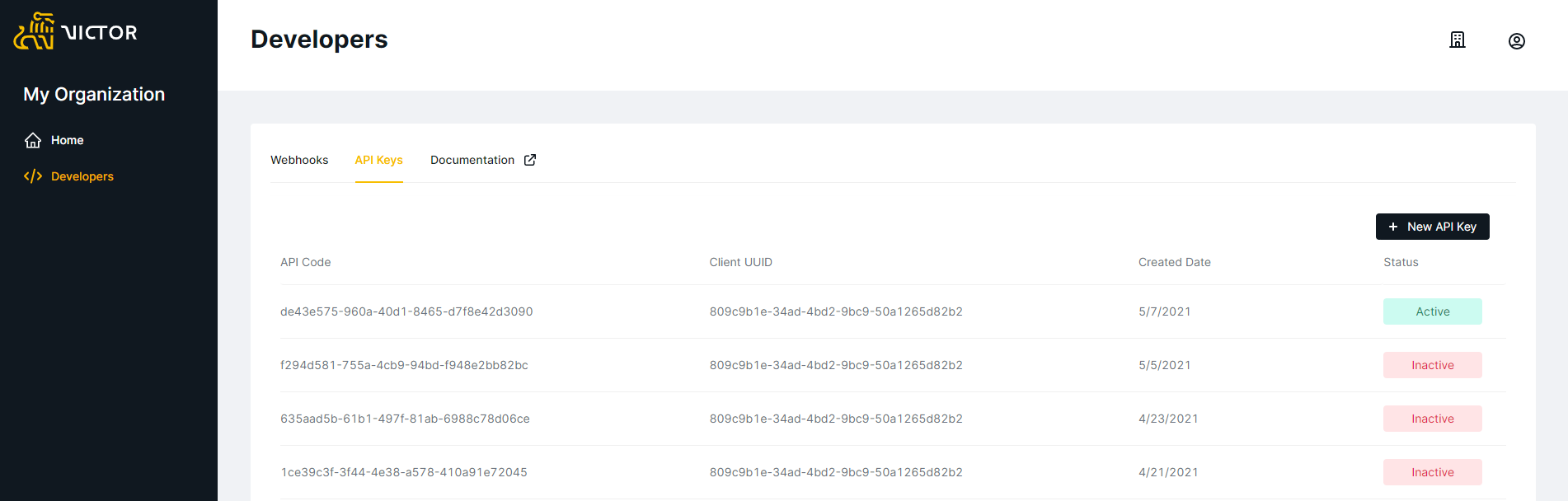
In order to generate your API Key, login to the Client Portal, navigate to My Organization from the Home menu and select the Developer menu item from left-hand options.\
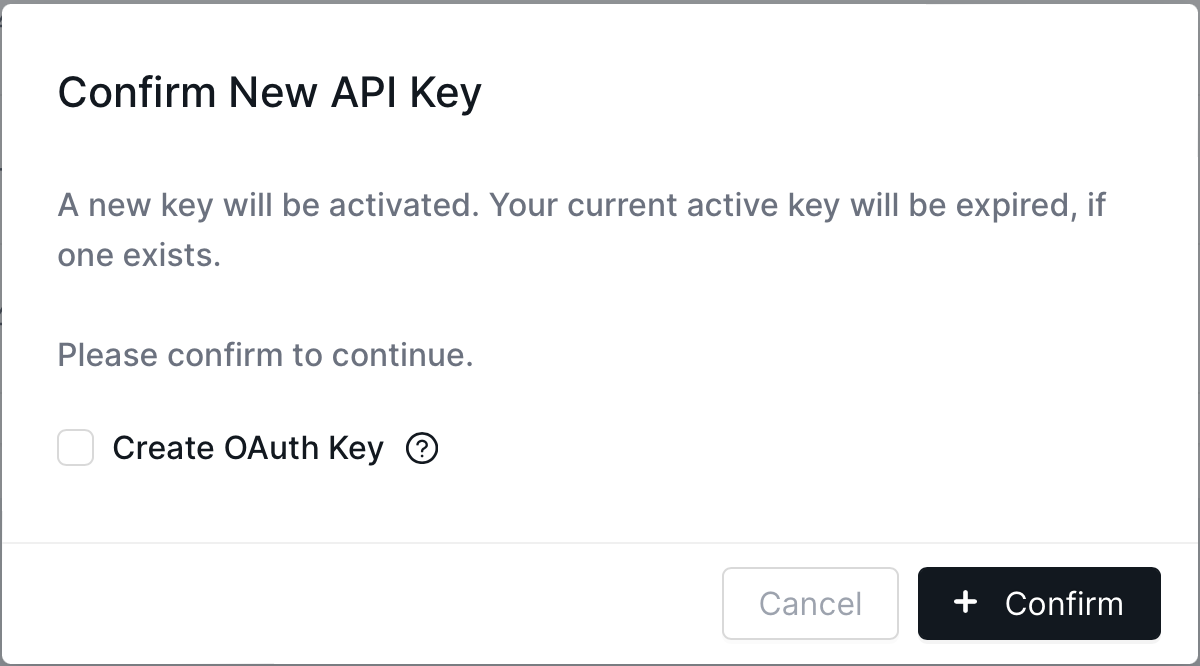
API Key TypesOAuth: By checking the "Create OAuth Key" within the "New API Key" modal, an OAuth API Key will be created. This is the preferred method of authentication and the instructions for using this key can be found in the below section, "Using an OAuth Token".
Developers Page
New API Key Modal
Using an OAuth Token
After generating an OAuth API Key, the client ID and client secret can be used to obtain a valid JWT token. Note the token will automatically expire and no longer be valid after the expires epoch timestamp (in milliseconds) returned in the access token response has been reached. Once a token has expired, a new token must be requested.\
Requesting an Access Token
A JWT access token can be requested using the /v2/auth/token API endpoint by providing the client ID and client secret in the request body. A Sample request and sample response are shown below:
Sample Request
{
"client_id": "<your-client-id>",
"client_secret": "<your-secret>"
}Sample Response
{
"access_token": "<access-token-value>",
"token_type": "<token-type e.g. Bearer>",
"expires": 1683308669000
}Using the Access Token
The access token must be included in all requests to the Victor API. To use the access token, include it in the request as an Authorization header prefixed by the token_type e.g. Bearer as shown in the example below.
--header 'Authorization: Bearer <access-token-here>'Updated 5 months ago
